Privilege Promiscuity Exposes Need for Zero-Trust Approach to Admin Rights
– Andrew Milroy, VP and Head of Research at Focus Network
Introduction
Recent cyberattacks have shown that privileged accounts are gold mines for malicious actors. Some of the largest breaches in APAC have been caused by stolen privileged credentials being used, which have given attackers access to highly sensitive data. When inside systems, such attacks often offer persistent access to valuable corporate resources and pose a massive risk to organisations. It often takes months or sometimes years, to detect such attacks. In other words, once authentication has been breached and credentials are obtained by an adversary, moving laterally, persistence, and accessing multiple resources are too easy.
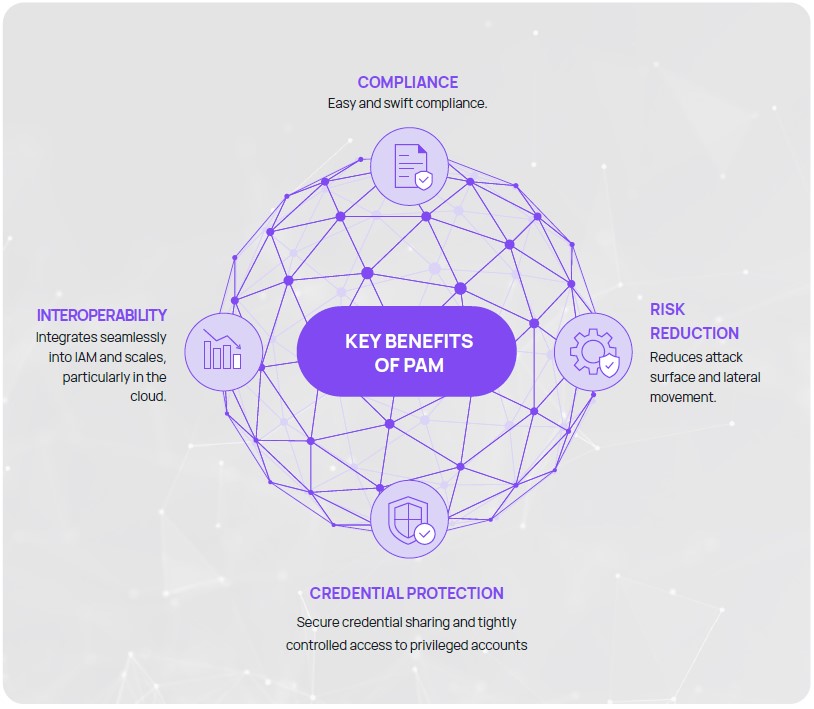
The most privilege is not always granted to the most senior employees. Administrative and personal assistants often have the greatest access to corporate resources. They are the low hanging fruit for attackers — they are usually among the least well prepared to deal with breaches and attacks such as phishing emails. Privilege promiscuity like this creates challenges around not only Privileged Access Management (PAM), but also other digital risk controls. PAM can mitigate cybersecurity risk substantially if security processes strictly enforce the principle of least privilege. Key benefits of PAM are shown in Figure 1.
Key Benefits of PAM
Scaling PAM is Complex

Think of PAM as a way of stopping people from abusing privilege. Imagine that you need a plumber to repair your kitchen sink. The plumber is granted access to your house through the front door and is guided to the kitchen. The plumber is monitored and exits the kitchen as soon as the job is completed. The plumber then leaves the house. The worst outcome is a shoddy job or perhaps the theft of small pieces of cutlery or a few fridge magnets. In other words, the plumber’s access has been managed and privilege was only granted as needed. This is good PAM.
Bad PAM is a scenario where the plumber is granted access to your home, and nobody is in to monitor the plumber’s activities. The plumber could be honest and might come in and do the job and then depart. But, there is a significant risk that the plumber takes advantage of the privileged access granted. The plumber has access to all the rooms in the house and all the items in the house. The plumber can invite other people into the house, including a friend who can remove and copy data from all resident hard drives in the house. This access enables the plumber to steal credit cards, jewellery, PII, credentials and more.
Now, imagine that there are hundreds of plumbers and other workers entering and exiting a house at varying times and for different purposes — each with distinct tasks and a need for access to different rooms and items. This is the challenge faced by security operations — there are often hundreds or thousands of users with differing privileges to manage. Organisations are struggling to keep up with the sheer scale of the PAM challenge with all its moving parts. PAM also needs to consider the ongoing change in roles and responsibilities of staff, which directly impacts requirements for privileged access.
Privilege Sprawl and Privilege Overkill is Rife in APAC
Once an adversary breaches a privileged account, and is able to move laterally, they can access email accounts, intellectual property, employee data, customer data, sales data, invoicing approvals, expense approvals and many other systems and processes. In addition to being exposed to short term financial risk, an organisation also faces operational, legal and reputational risk from such a breach.
The attacker can unload ransomware or other malware to sabotage operations — this has been a common approach in recent attacks. They can also steal PII and credentials and sell them or use them to cause reputational and legal damage to the victim. Stolen credentials are also commonly sold on the dark web. It is important to continuously monitor dark web activity to determine if credentials from your organisation are being made available.
Privilege sprawl is common in APAC organisations. IT departments often struggle to keep track of who has access to what. Worse, IT departments typically over-provision their stakeholders with access.
They are usually more concerned with getting positive feedback from the business for the IT resources they provide than in aggressive risk management. Most organisations prioritise making day-to-day business activities frictionless —especially for users that are likely to have the most privileges.
Cybersecurity tends to be addressed reactively when a vulnerability becomes apparent to senior business leaders or when an attack occurs.
Specialised (PAM) solutions have emerged to mitigate the risk associated with unauthorised account access. The term privileged access management is a bit of misnomer. Today’s organisations need to ensure that all access is managed correctly. With an expanding number of devices, bots and people, accessing corporate resources, the scope of PAM solutions is much broader than managing privileged accounts alone. Nevertheless, some privileged accounts tend to have much more access to resources than other accounts, and they are commonly targets for attackers.
A Zero-Trust Approach to PAM is Necessary
Organisations must ensure that several key practices are enforced by their PAM solutions.
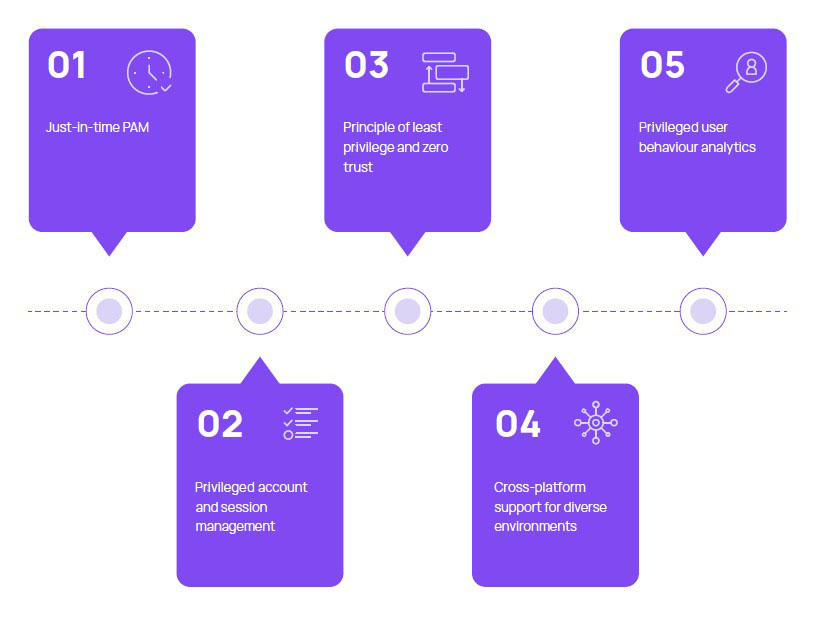
Figure 2 illustrates some of the essential PAM practices.
Figure 2
Five Essential PAM Practices
Critically, they need to take a zero-trust approach to PAM and align it with other zero-trust controls.
Just in time access (JITA) needs to become the norm, ending persistent privileged access. Access needs to be granted for the minimum amount of time with the minimum rights required. Zero standing privilege needs to be the default state of systems and networks. Access must be denied as soon as necessary work is complete and only provisioned when needed again. Behavioural analytics is key to detecting privilege abuse rapidly and containing the threat. Cross platform support for diverse environments is also important given they heterogeneous nature of today’s IT architectures. These approaches are needed for risk management but few organisations in APAC follow all of these practices strictly. The sheer number of moving parts involved in enforcing and managing privileged access makes it particularly onerous — this is where modern PAM solutions play a role.
Disclaimer
Whilst reasonable efforts have been made to ensure that the information and content of this product was correct as at the date of first publication, neither Focus Network nor any person engaged or employed by Focus Network accepts any liability for any errors, omissions or other inaccuracies.
Readers should independently verify any facts and figures as no liability can be accepted in this regard – readers assume full responsibility and risk accordingly for their use of such information and content.
Any views and/or opinions expressed in this product by individual authors or contributors are their personal views and/or opinions and do not necessarily reflect the views and/or opinions of Focus Network.



